Rest easy with around the clock protection.
Secured devices. Safe content. Productive environment
With machine learning, be confident suspicious behavior will be flagged and analyzed by threat hunters.
Always on our post.
Always on our watch.
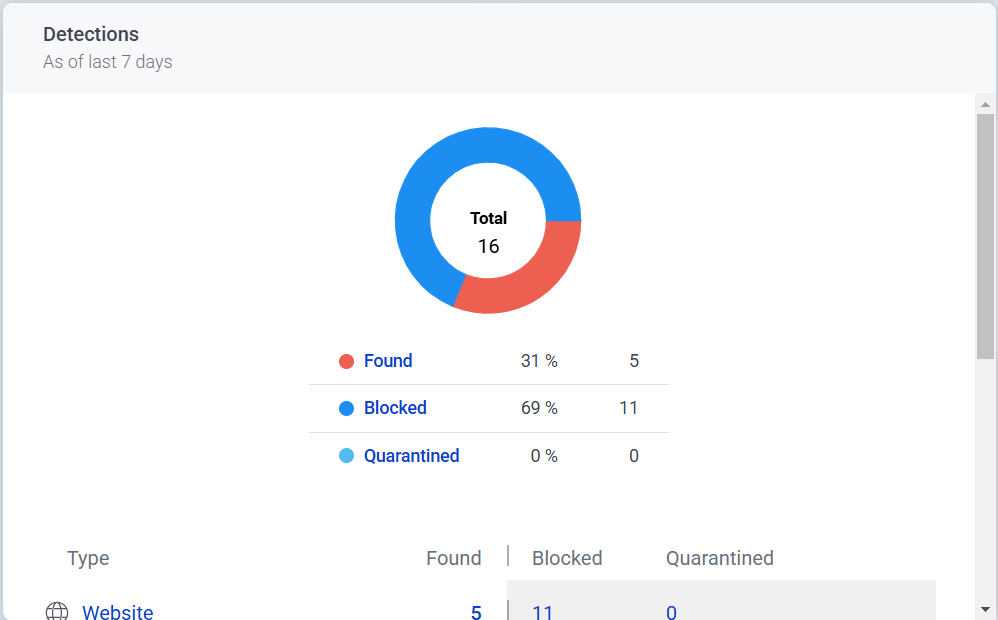
Extensive antivirus and detection system with built in AI machine learning protection. Providing 24/7 protection
Device notifications alert you on actions taken in real time.
Protect with intentionality.

Endpoint Protection
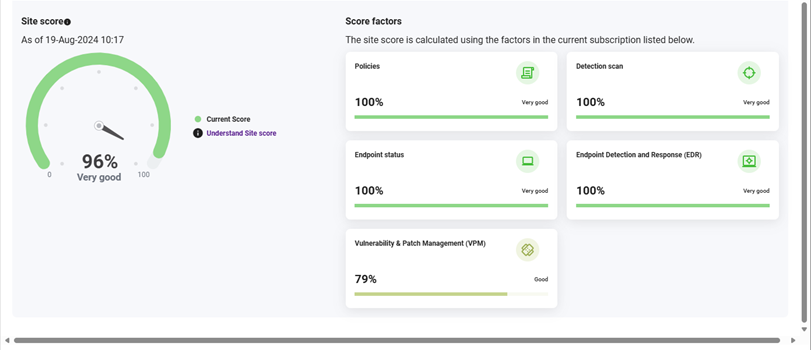
Overall client device scoring provides valuable insights to the security team.
Families are the foundation to building security.
Take your stand
Rebuilding the wall of security
around your family.
Machine Learning
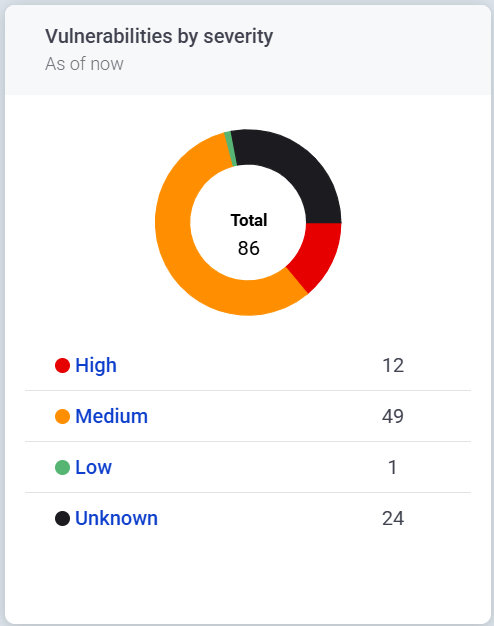
Databases that are kept up to date will consistently outpace newer and more sophisticated virus signatures.
Web browser guard.
Provides protection against decoy websites, phishing, and ad trackers. Includes a blacklist for harmful websites targeting children and teenagers.
Incident Response and Endpoint Protection
Powerful Antivirus software equipped with a stack of security measures.
Family Basic
— up to 5 devices
- Next Gen Antivirus for devices
- Endpoint Protection and Incident Response
- Web Browser Protection
- Blacklisting and App Blocking
- Protection for Android and IOS devices, Windows and MAC
- DNS Filtering
$15 per device – Monthly
Family Premium
— includes all 5 devices and basic plan services
- Includes remote IT services for your Windows and IOS Laptops and Computers
$45 – Monthly


